[EVM: Zero to Hero] All About Accounts
Explaining what powers the worlds most valuable blockchains
Welcome to Article 2 of EVM: Zero to Hero, the easiest way to learn about what powers the world’s most valuable blockchains!
In case you missed it, here’s a summary what we covered in Article 1:
Blockchain fundamentals: transactions and decentralized systems
What the EVM is
How the EVM runs smart contracts
How EVM compatibility standardizes the developer experience across blockchains
In this article, we’ll go over the different types of EVM accounts that are used to authenticate transactions, store smart contracts, and much more. Let’s dive in!
Introducing Accounts
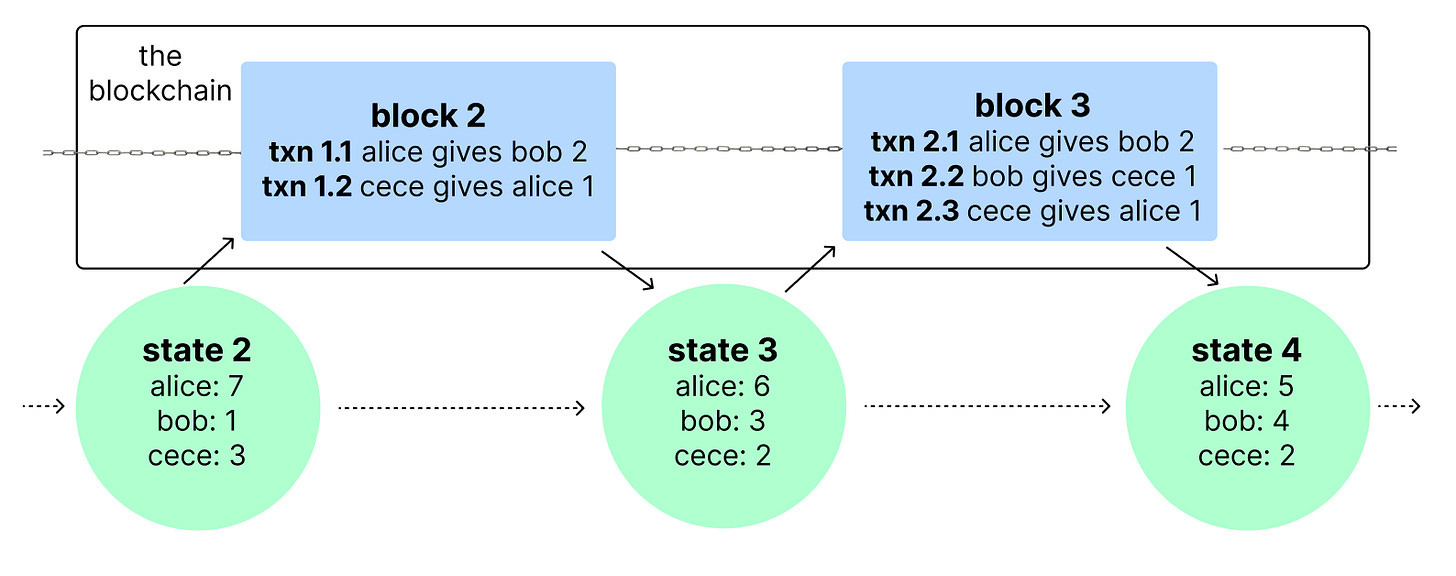
In the first article of EVM: Zero to Hero, we talked about how transactions trigger state changes on the blockchain.
While the blockchain itself is made up of transactions, it’s often useful to look at the blockchain in the context of its implied states (the green circles). These implied states are more intuitive because they represent a concrete snapshot of the blockchain rather than a list of transactions (the blue boxes).
Our example above is slightly simplified. On EVM compatible blockchains, each item in the green circles is called an account. Each account has its own unique identifier, called an address, which points to the data it owns. For example, in state 2 above, “alice” is an address that owns 7 units of cryptocurrency.
The EVM supports two types of accounts:
Externally Owned Accounts (EOAs)
Contract Accounts (better known as a smart contracts)
But First… Some Crypto(graphy)
Before we can dig into EVM accounts, it’s helpful to get a few cryptography concepts down first.
The need to send secret messages has been a problem since humans have been communicating. One well-known way to send secret messages is Caesar’s Cipher:
Caesar’s Cipher is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. This shift is always the same for a given cipher message. For example, with a right shift of 2, C would be replaced by E, B would become D, and so on.
Fast forward a couple thousand years, and the state of the art is asymmetric key encryption.
There are tons of great resources on this topic, so I’ll be brief:
Asymmetric encryption requires a private and a public key. These keys are long sequences of random characters
Private keys should be kept secret, while public keys can be shared with anyone
One private key corresponds to one public key
It’s easy to get a public key from a private key, but it’s essentially impossible to get a private key from a public key. Learn more here
Anyone can generate a key pair. The odds of you generating one that matches someone else’s is ~0%
With these two keys, you can take a few actions:
Encrypt. Using a public key, you can “encrypt” data by making it impossible to read by anybody besides the private key holder.
Sign. Using the private key, you can “sign” data. This proves that the data came from you, and anyone can verify this fact by using the public key.
🚨 Confusion alert 🚨
This stuff isn’t easy! If asymmetric encryption isn’t clear yet, check out Wikipedia or this youtube video.
Externally Owned Accounts
Externally Owned Accounts are the accounts you typically hear about when someone says “I have 20 ETH.” The address of an EOA is a public key, and funds of an EOA can only be moved if the account owner signs a message with their corresponding private key. EOA addresses point to how much currency it owns.
EOAs are dangerous because their private keys are a single point of failure. If you lose the private key, it’s impossible to get into your account again. This has resulted in billions of dollars in lost cryptocurrency!
💭 More information 💭
Applications that help you manage your crypto are called wallets and include products like Metamask and Rainbow. Wallets are typically EOAs under the hood, meaning that they help you manage your private key.
The final thing to note about EOAs is that they are the only type of account that can initiate transactions. We’ll explain why later on, but remember this important fact!
Contract Accounts
Contract accounts (more commonly known as smart contracts) store code that runs directly on EVM-compatible blockchains. From the last article:
Smart contracts are powerful because they enable developers to create complex applications on the blockchain… examples include financial purposes, gaming, healthcare, real estate…
Like EOAs, smart contracts also have an identifying address, but they are not controlled by a private key. So what actually controls smart contracts? The code.
If you’re confused about what that means, don’t sweat it. I was too! Let me explain:
Smart contracts are just programs that run on blockchains. Developers write code to indicate how they want smart contracts to work
Developers can use their EOAs to create smart contracts via a transaction
The code is highly customizable, and the developer decides who can access and modify it. For example, some smart contracts deployed on the blockchain can never be updated. More on this in future articles!
So what’s the deal with this transaction initiation?
It’s important to emphasize that smart contracts cannot initiate transactions. This is because the EVM only supports transactions that have been signed with a private key. Smart contracts don’t have private keys, so they can’t create transactions! Therefore, only EOAs can create transactions that in turn create and call smart contracts.
Going Beyond EOA Wallets
As we’ve learned, each type of EVM account has its pros and cons:
Smart Contract Wallets (SCWs) address the inflexibilities of “regular” wallets (EOAs). SCWs use the customizability of smart contracts to provide an enhanced wallet experience. In the next article, we’ll be covering SCWs as well as future EVM upgrades that will give smart contracts the power to initiate transactions themselves!
Recap
Enjoyed this article? The next in this series is article is out now!
In today’s article, we covered:
Some basic cryptography: Caesar’s cipher and asymmetric key encryption
The two EVM account types: EOAs and contract accounts
The pros and cons of each account type
We’d love to hear what you think about Article 2 of EVM: Zero to Hero! It was definitely more technical than the last one, but we hope you were able to understand it. If you have any questions, don’t hesitate to reach out in the comments, on Twitter, or via email at shekar@ramaswamy.org.
Next up, we’re covering smart contract wallets in more depth. We’ll also analyze one of the most important updates coming to the EVM!
Further Reading
More on use cases for smart contracts